If you plan to use Rstudio outside of your internal network (or even from an external hosted server) it is best to use nginx as a proxy, and even better by implementing valid certificates.
To configure nginx there are some good tutorials online available – this one
https://www.digitalocean.com/community/tutorials/how-to-secure-nginx-with-let-s-encrypt-on-centos-7
describes pretty well what has to be done. letsencrypt is delivering trusted certificates – they have to be renewed every three months, but this can be automated (described in the article above as well).
If you follow the steps above, request and implementation of a SSL protected setup for your rstudio setup (and later one shiny) is quite simple.
# certbot certonly --standalone --preferred-challenges http --http-01-port 8080 -d rstudio.7o9.de
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator standalone, Installer None
Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for rstudio.7o9.de
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/rstudio.7o9.de/fullchain.pemAs we’ve got now our certificates, we are ready to configure the SSL setup for our rstudio access.
########### SSL config for rstudio.7o9.de
server {
# SSL only
listen 443 ssl http2;
server_name rstudio.7o9.de;
# Location of letsencrypt certificates
ssl_certificate /etc/letsencrypt/live/rstudio.7o9.de/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/rstudio.7o9.de/privkey.pem;
# Optimized SSL session cache
# ssl_session_cache shared:SSL:40m;
# ssl_session_timeout 4h;
# Enable session tickets (as an alternative to ssl session cache)
ssl_session_tickets on;
# Only support the latest SSL protocol
ssl_protocols TLSv1 TLSV1.1 TLSv1.2;
# Strict Transport security
add_header Strict-Transport-Security "max-age=31536000; preload" always;
# Supported SSL ciphers
ssl_ciphers ECDH+AESGCM:ECDH+AES256:ECDH+AES128:DH+3DES:!ADH:!AECDH:!MD5;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/nginx/certs/lets-encrypt-x3-cross-signed.pem;
ssl_prefer_server_ciphers on;
# Forward to rstudio host
location / {
proxy_pass http://192.168.140.225:8787;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header X-Forwarded-Port 443;
proxy_set_header Host $host;
# Required to enable upload of larger files
client_max_body_size 128m;
# for web socket support
proxy_redirect http://localhost:8787/ $scheme://$host/;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_read_timeout 20d;
proxy_buffering off;
}
}
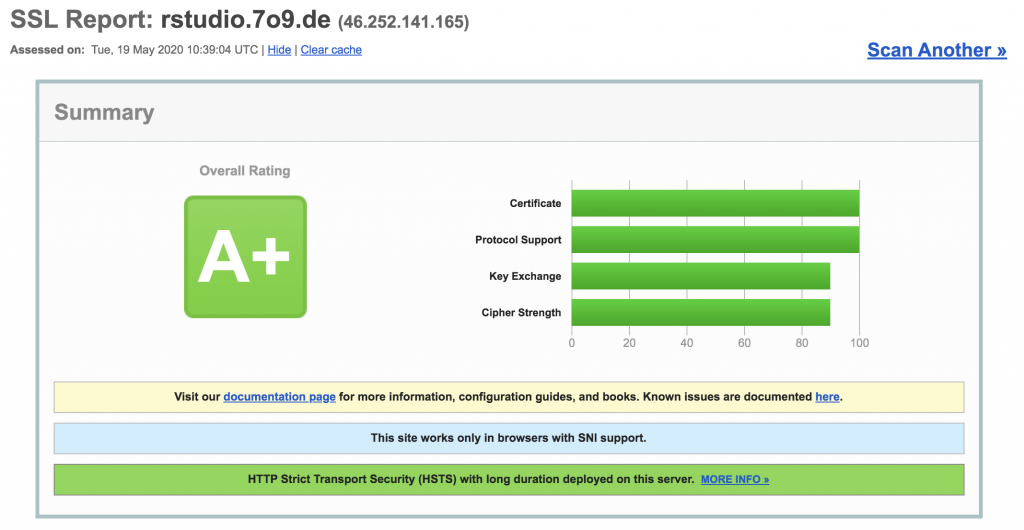
########## end of rstudio.7o9.de config To check if your setup is fine, just enter your URL here:
https://www.ssllabs.com/ssltest/analyze.html?d=rstudio.7o9.de
Yeah – Grade A+ – that’s nice.
and Chrome and all others are happy as well.
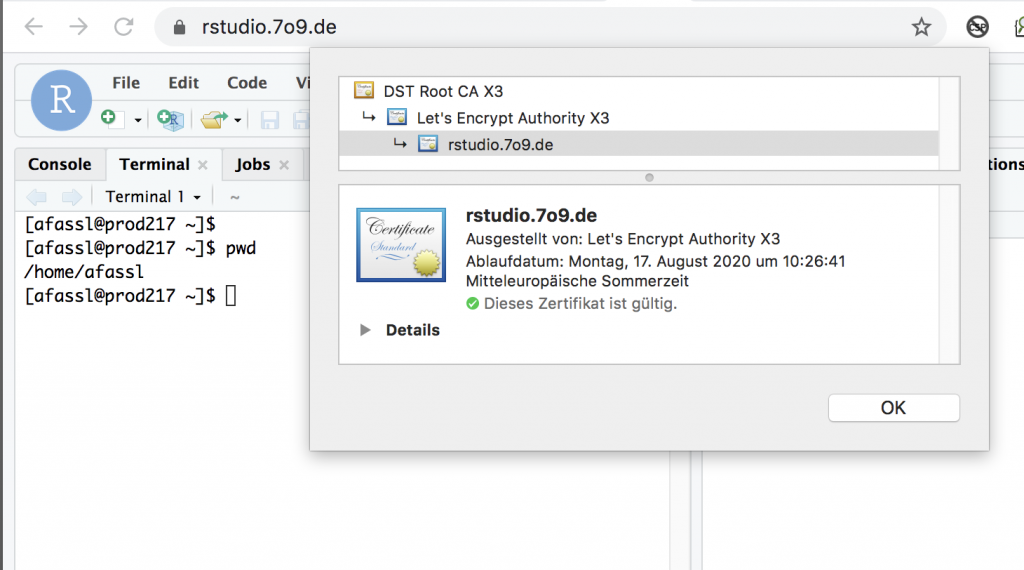
Again – don’t use easy to guess passwords for your rstudio account. Part of the rstudio is a fully web based console – all the ubiquitous password crawlers are more than happy to find another „test/test“ login. And they will crawl your site for sure. 100% guaranteed!